Linux GRE Configuration
GRE is a tunneling protocol that encapsulates various network layer protocols inside point-to-point connections. It is used to create virtual private networks (VPNs) and to transport packets over IP networks.
- Encapsulation: GRE encapsulates packets within an outer IP packet, allowing the transport of protocols that might not be natively supported by the underlying network.
- Simplicity: GRE is straightforward and lightweight, making it easy to implement.
- Use Case: Commonly used for creating VPNs, connecting geographically dispersed networks, and enabling compatibility between different network protocols.
Required Linux Modules
root@dent-1:~# lsmod
Module Size Used by
ip_gre 32768 0
gre 16384 1 ip_gre
Basic GRE configuration
Topology
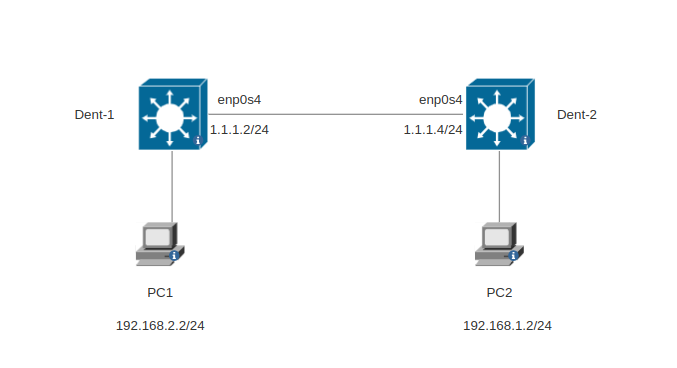
Configuration
- config
enp0s4link on both devices with the required ip addresses. - create
tun1GRE link on both sides. - add route to the remote destination and set
tun1as nexthop device.
- ONM-CLI
- IPROUTE2
- NETCONF
dent-1(config-links-iproute2)# link enp0s4
dent-1(config-[name='enp0s4'])# ip 1.1.1.2/24
dent-1(config-[name='enp0s4'])# admin-status up
dent-1(config-[name='enp0s4'])# exit
dent-1(config)# links-iproute2
dent-1(config-links-iproute2)# gre tun1
dent-1(config-gre[name='tun1'])# admin up
dent-1(config-gre[name='tun1'])# tunnel-info local 1.1.1.2
dent-1(config-gre[name='tun1'])# tunnel-info remote 1.1.1.4
dent-1(config-gre[name='tun1'])# tunnel-info pmtudisc on
dent-1(config-gre[name='tun1'])# exit
dent-1(config-links-iproute2)# exit
dent-1(config)# routes-iproute2
dent-1(config-routes-iproute2)# route 192.168.1.0/24
dent-1(config-[prefix='192.168.1.0/24'][table='main']# nexthop tun1
dent-1(config-nexthop[dev='tun1'])# commit
ip address add 1.1.1.2/24 dev enp0s4
ip link add name tun1 up type gre local 1.1.1.2 remote 1.1.1.4
ip route add 192.168.1.0/24 table main metric 0 tos default nexthop dev tun1 weight 1
<config>
<links xmlns="urn:okda:iproute2:ip:link" xmlns:yang="urn:ietf:params:xml:ns:yang:1" yang:operation="none">
<link>
<name>enp0s4</name>
<ip>
<address>1.1.1.2/24</address>
</ip>
</link>
<gre yang:operation="create">
<name>tun1</name>
<admin-status yang:operation="create">up</admin-status>
<tunnel-info yang:operation="create">
<local yang:operation="create">1.1.1.2</local>
<remote yang:operation="create">1.1.1.4</remote>
<pmtudisc yang:operation="create">on</pmtudisc>
</tunnel-info>
</gre>
</links>
<routes xmlns="urn:okda:iproute2:ip:route" xmlns:yang="urn:ietf:params:xml:ns:yang:1" yang:operation="none">
<route yang:operation="create">
<prefix>192.168.1.0/24</prefix>
<table>main</table>
<metric>0</metric>
<tos>default</tos>
<netns>1</netns>
<nexthop yang:operation="create">
<dev>tun1</dev>
</nexthop>
</route>
</routes>
</config>
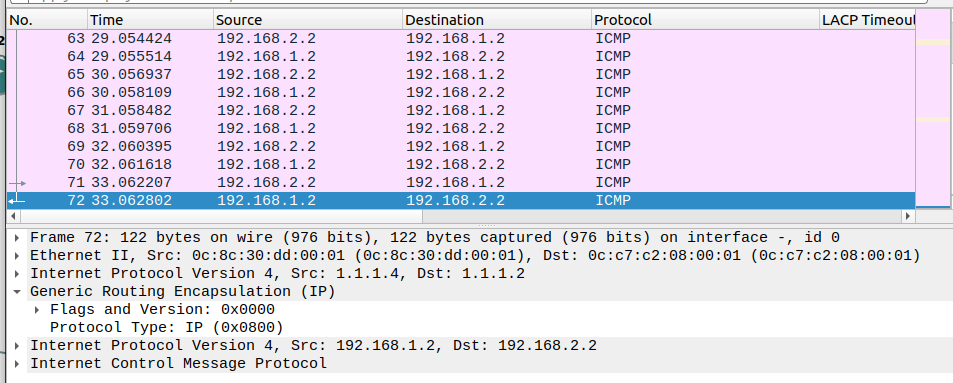
Verify
- If we ping from
PC1toPC2we can see that the traffic is encapsulated with GRE tunnel.