Linux Network Namespace Configuration
A Linux network namespace provides an isolated network environment, allowing multiple instances of network stacks to coexist on a single host. each namespace has its own interfaces, IP addresses, FDB(L2 forwarding DB). and routing tables, ensuring separation of network configurations. This isolation is crucial for containerization and virtualization, ensuring separate network configurations within shared hardware.
Network namespace is equivalent to VPNs or VRFs in traditional network devices.
VETH links are used to interconnect different NETNS(network namespace) and achieve connectivity
between them.
Unlike Linux VRF links which provide routing table isolation for it's slave devices, the network namespace has a complete isolation of the linux network stack.
Basic Network Namespace configuration
In this document, we will create two netns(network namespace), VPN10 and VPN20,
then we will create two VETH links to interconnect the two netns to achive connectivity
between them.
Topology
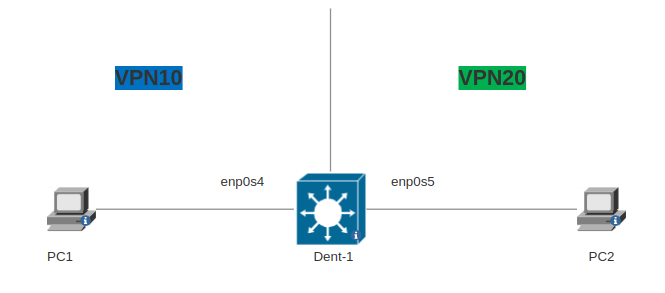
Configuration
- Create two netns (
vpn10andvpn20), then we - Add
enp0s4link tovpn10netns andenp0s5link tovpn20netns.
- ONM-CLI
- IPROUTE2
- NETCONF
dent-1(config)# netnses-iproute2
dent-1(config-netnses-iproute2)# netns vpn10
dent-1(config-netnses-iproute2)# netns vpn20
dent-1(config-netnses-iproute2)# exit
dent-1(config)# links-iproute2
dent-1(config-links-iproute2)# link enp0s4
dent-1(config-[name='enp0s4'])# netns vpn10
dent-1(config-[name='enp0s4'])# ip 192.168.10.10/24
dent-1(config-[name='enp0s4'])# admin-status up
dent-1(config-[name='enp0s4'])# exit
dent-1(config-links-iproute2)# link enp0s5
dent-1(config-[name='enp0s5'])# netns vpn20
dent-1(config-[name='enp0s5'])# ip 192.168.20.20/24
dent-1(config-[name='enp0s5'])# admin-status up
dent-1(config-[name='enp0s5'])# commit
ip netns add vpn10
ip netns add vpn20
ip link set name enp0s4 up netns vpn10
ip -n vpn10 address add 192.168.10.10/24 dev enp0s4
ip link set name enp0s5 up netns vpn20
ip -n vpn10 address add 192.168.10.10/24 dev enp0s4
<config>
<netnses>
<netns>
<name>vpn10</name>
</netns>
<netns>
<name>vpn20</name>
</netns>
</netnses>
<links>
<link>
<name>enp0s4</name>
<admin-status>up</admin-status>
<netns>vpn10</netns>
<ip>
<address>192.168.10.10/24</address>
</ip>
</link>
<link>
<name>enp0s5</name>
<admin-status>up</admin-status>
<netns>vpn20</netns>
<ip>
<address>192.168.20.20/24</address>
</ip>
</link>
</links>
</config>
Now we have two PCs in different netns, if we check the fdb/arp table we can see that each link PC ip belong to different netns
dent-1# show config-running neighbors-iproute2
neighbor 192.168.20.1 netns vpn20
dev enp0s5
router false
use false
managed false
extern_learn false
lladdr e6:70:03:8d:7e:09
nud reachable
neighbor 192.168.10.1 netns vpn10
dev enp0s4
router false
use false
managed false
extern_learn false
lladdr b6:1d:6e:03:0e:e6
nud stale
dent-1#
Veth Configuration
Now if we want to have connectivity between the two different netns, we will need
to create a veth link for each netns, and interconnect them.
To achieve this we do the following:
- Create
veth10and setveth20as its peer. - add each veth to it's netns.
- add route for each vpn client subnet (192.168.10.0/24 for vpn10) and (192.168.20.0/24 for vpn20). and the nexthop for those route are the veth interfaces.
- ONM-CLI
- IPROUTE2
- NETCONF
dent-1(config-links-iproute2)# link veth10
dent-1(config-[name='veth10'])# type iproute2-ip-link:veth
dent-1(config-[name='veth10'])# virtual_peer_name veth20
dent-1(config-[name='veth10'])# ip 1.1.1.9/30
dent-1(config-[name='veth10'])# admin-status up
dent-1(config-[name='veth10'])# netns vpn10
dent-1(config-[name='veth10'])# exit
dent-1(config-links-iproute2)# link veth20
dent-1(config-[name='veth20'])# type iproute2-ip-link:veth
dent-1(config-[name='veth20'])# netns vpn20
dent-1(config-[name='veth20'])# ip 1.1.1.10/30
dent-1(config-[name='veth20'])# admin-status up
dent-1(config-[name='veth20'])# virtual_peer_name veth10
dent-1(config-[name='veth20'])# exit
dent-1(config)# routes-iproute2
dent-1(config-routes-iproute2)# route 192.168.20.0/24 netns vpn10
dent-1(config-[prefix='192.168.20.0/24'][netns='vpn10']# nexthop veth10
dent-1(config-[prefix='192.168.20.0/24'][netns='vpn10']# exit
dent-1(config-routes-iproute2)# route 192.168.10.0/24 netns vpn20
dent-1(config-[prefix='192.168.10.0/24'][netns='vpn20']# nexthop veth20
dent-1(config-[prefix='192.168.10.0/24'][netns='vpn20']# commit
ip -n vpn10 link add name veth10 up type veth peer name veth20
ip -n vpn10 address add 1.1.1.9/30 dev veth10
ip -n vpn10 link add name veth20 up type veth peer name veth10
ip -n vpn10 address add 1.1.1.10/30 dev veth20
ip -n vpn10 route add 192.168.20.0/24 nexthop dev veth10
ip -n vpn20 route add 192.168.10.0/24 nexthop dev veth20
<config>
<links xmlns="urn:okda:iproute2:ip:link" xmlns:yang="urn:ietf:params:xml:ns:yang:1" yang:operation="none">
<link>
<name>veth10</name>
<admin-status>up</admin-status>
<netns>vpn10</netns>
<ip>
<address>1.1.1.9/30</address>
</ip>
<type>veth</type>
<virtual_peer_name>veth20</virtual_peer_name>
</link>
<link>
<name>veth20</name>
<admin-status>up</admin-status>
<netns>vpn20</netns>
<ip>
<address>1.1.1.10/30</address>
</ip>
<type>veth</type>
<virtual_peer_name>veth10</virtual_peer_name>
</link>
</links>
<routes xmlns="urn:okda:iproute2:ip:route" xmlns:yang="urn:ietf:params:xml:ns:yang:1" yang:operation="none">
<route>
<prefix>192.168.20.0/24</prefix>
<table>254</table>
<metric>0</metric>
<tos>default</tos>
<netns>vpn10</netns>
<nexthop>
<dev>veth10</dev>
</nexthop>
</route>
<route yang:operation="create">
<prefix>192.168.10.0/24</prefix>
<table>254</table>
<metric>0</metric>
<tos>default</tos>
<netns>vpn20</netns>
<nexthop yang:operation="create">
<dev>veth20</dev>
</nexthop>
</route>
</routes>
</config>
Now we should have connectivity between PC1 and PC2.
PC1> ping 192.168.20.1
PING 192.168.20.1 (192.168.10.1) 56(84) bytes of data.
64 bytes from 192.168.20.1: icmp_seq=1 ttl=64 time=0.878 ms
64 bytes from 192.168.20.1: icmp_seq=2 ttl=64 time=1.00 ms
64 bytes from 192.168.20.1: icmp_seq=3 ttl=64 time=1.16 ms
64 bytes from 192.168.20.1: icmp_seq=4 ttl=64 time=1.07 ms
To allow the communication between PC1 and PC2 from different netns,
we need to enable net.ipv4.ip_forward on each netns:
ip netns exec vpn10 sysctl -w net.ipv4.ip_forward=1ip netns exec vpn20 sysctl -w net.ipv4.ip_forward=1